Mastering Security Settings: How to Configure Your Firewall via 192.168.l0.1
In the highly dangerous digital world of today, network security is crucial. Configuring the router’s firewall, which is often accessed using the IP address 192.168 l0 1, is essential to this endeavor. This thorough guide will walk you through the complexities of firewall setup and optimization, illuminating the way to strengthen your network defenses.
The Importance of Firewalls
By filtering incoming and outgoing network traffic according to preset security rules, firewalls act as barriers to your internet connection. They oversee and control access points, preventing unwanted attempts and permitting secure communications to flow through. They essentially serve as your network’s first line of defense against outside threats, making sure that malicious activity does not sneak into your system unnoticed.
Configuration
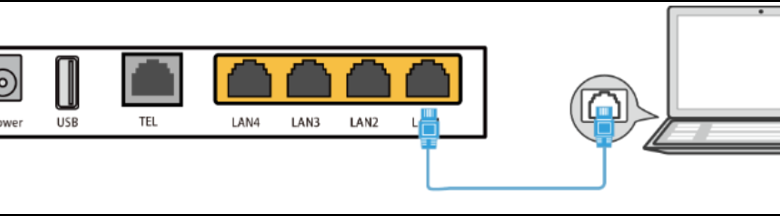
When configuring your firewall, regardless of your router’s specific make and model, a universal framework applies after you log in. Begin by navigating to the firewall section within your router’s administration menu, commonly found under titles like “Firewall,” and “Security,” nested within “Advanced” or “Setup” sections. Next, ensure that the built-in firewall is activated—a simple toggle switch often labeled “Enable Firewall”—to instantly apply default rules that deter unwanted traffic. Then, set up zone rules to distinguish between your internal network (LAN) and the internet (WAN), imposing tighter controls on external access while easing restrictions for trusted local devices. Manage access through Access Control Lists (ACLs), employing MAC address filtering to whitelist authorized devices and IP address filtering to selectively block or allow traffic. Enhance your firewall’s capability by enabling Stateful Packet Inspection (SPI), which analyzes packet states for deeper threat detection. Regularly updating firewall rules becomes crucial given the fluid nature of cybersecurity, keeping abreast of new threats, and applying timely security patches. Lastly, augment your defensive posture by activating the Intrusion Prevention System (IPS) if available on your router, adding a proactive barrier against malware and potential attacks.
Tips for Better Security
1. Be Alert of Port Scanning
For technology-adept users aiming to fortify their network’s defenses, several sophisticated measures can significantly elevate security protocols. One critical step involves enhancing port scanning protection. This entails systematically blocking all non-essential ports, thus minimizing exposure to potential threats. Moreover, engaging stealth mode renders your router virtually invisible to unsolicited scan attempts, providing an additional layer of obscurity to outsiders.
2. Filter the DNS
Incorporating DNS filtering is another potent strategy. Whether opting for a reputable third-party DNS provider or leveraging native capabilities offered by your router, this practice restricts access to known malicious websites. It acts as a sieve, intercepting requests destined for harmful domains, thereby safeguarding users from phishing scams and other web-based attacks.
3. Review the Log
Regular log monitoring stands out as a cornerstone of proactive network management. Scrutinizing firewall logs enables early identification of irregularities that might indicate attempted breaches or systemic vulnerabilities. By staying vigilant and promptly responding to any suspicious activity, network administrators can preemptively address issues before they escalate, reinforcing the network’s overall robustness against cyber threats. This multifaceted approach underscores the importance of combining technological solutions with diligent oversight to achieve optimal security outcomes.
Conclusion
In conclusion, by using 192.168.l0.1 to configure your router’s firewall, you can take control of your network’s security and protect it from a variety of online threats. You can feel secure knowing that your personal information and network integrity are safeguarded if you carefully follow these guidelines and keep an eye out for emerging cybersecurity trends. Recall that the fight against cybercrime is an ongoing one that necessitates ongoing alertness and flexibility. If you arm yourself with the information presented here, you’ll be ready to protect your virtual space.